
Photo by Julian Hochgesang on Unsplash
Carbanak/Cobalt Group: Analyzing the sophisticated cybercrime group targeting financial institutions.

The Carbanak/Cobalt Group, a highly sophisticated cybercrime syndicate, specializes in targeting financial institutions through meticulously planned and executed cyber attacks. Leveraging advanced techniques and tools, they have orchestrated numerous large-scale heists, posing a significant threat to global banking security.
COMPANY OVERVIEW:
The Carbanak/Cobalt Group's operations involve a blend of malware development, social engineering tactics, and intricate network infiltration strategies. Their targets primarily include banks and financial institutions, where they exploit vulnerabilities in both software and human defenses to gain access to sensitive systems and data.
WHAT HAPPENED (Technical Detail):
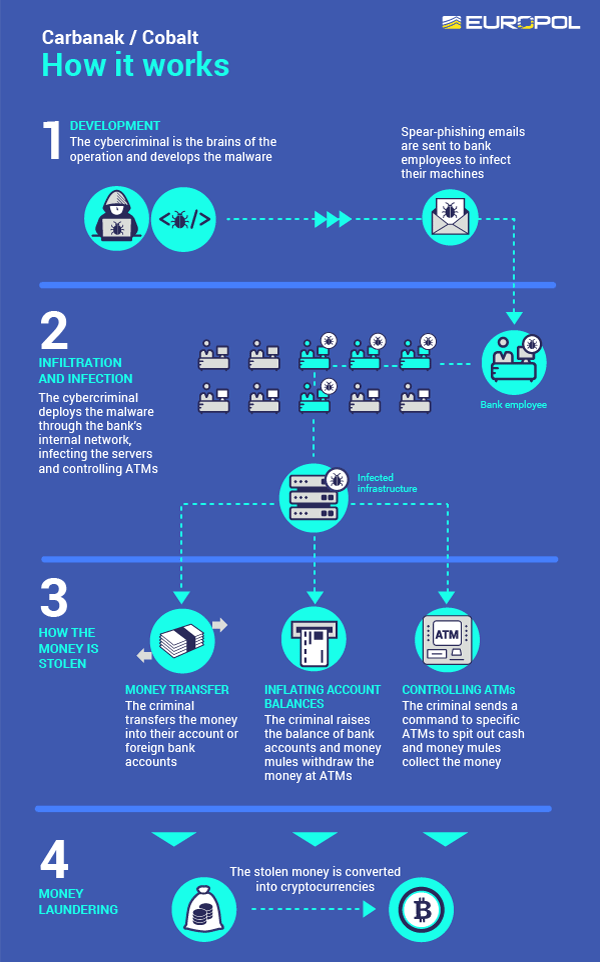
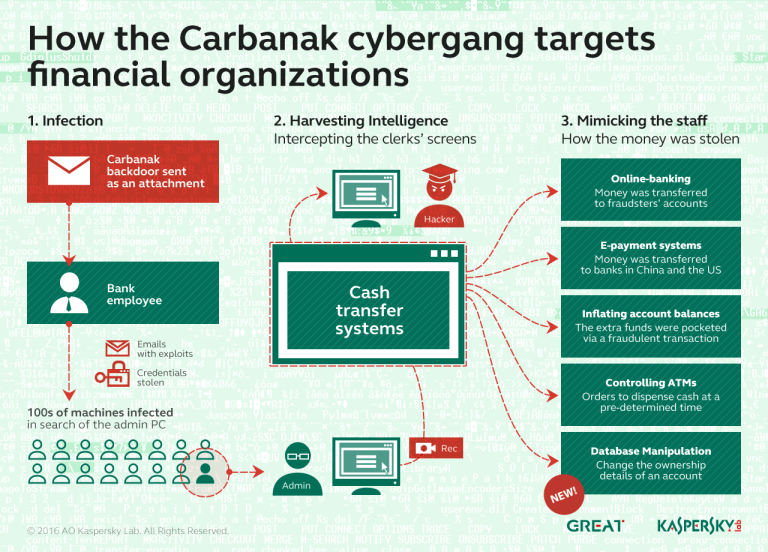
The Carbanak/Cobalt Group's operations typically begin with the initial compromise, often facilitated through spear-phishing emails containing malicious attachments or links. These emails are meticulously crafted to appear legitimate, enticing recipients to open attachments or click on links, thereby infecting their systems with malware.
Upon successful infiltration, the group deploys sophisticated malware, including variants of the Carbanak and Cobalt Strike families, tailored to evade detection by traditional security measures. This malware establishes persistence within the compromised network, allowing the attackers to maintain access and control over targeted systems.
Using command-and-control (C2) infrastructure, the attackers communicate with the compromised systems, issuing commands, and exfiltrating sensitive data. They leverage advanced techniques, such as living-off-the-land tactics and fileless malware, to evade detection and bypass security controls.
Once inside the network, the Carbanak/Cobalt Group conducts reconnaissance, mapping out the network topology and identifying high-value targets, such as servers containing financial data or systems with administrative privileges. They employ lateral movement techniques, exploiting vulnerabilities in unpatched software or weakly secured network segments, to expand their access and escalate privileges within the network.
Data exfiltration is carried out using encrypted communication channels or covert methods to avoid detection. The attackers carefully orchestrate their operations, minimizing their footprint and covering their tracks to evade detection for as long as possible.
Throughout the attack lifecycle, the Carbanak/Cobalt Group demonstrates a high degree of sophistication and adaptability, constantly evolving their tactics and malware to bypass security measures and maintain their operations. Their ability to blend social engineering tactics with advanced technical capabilities makes them a formidable adversary for financial institutions and cybersecurity professionals alike.
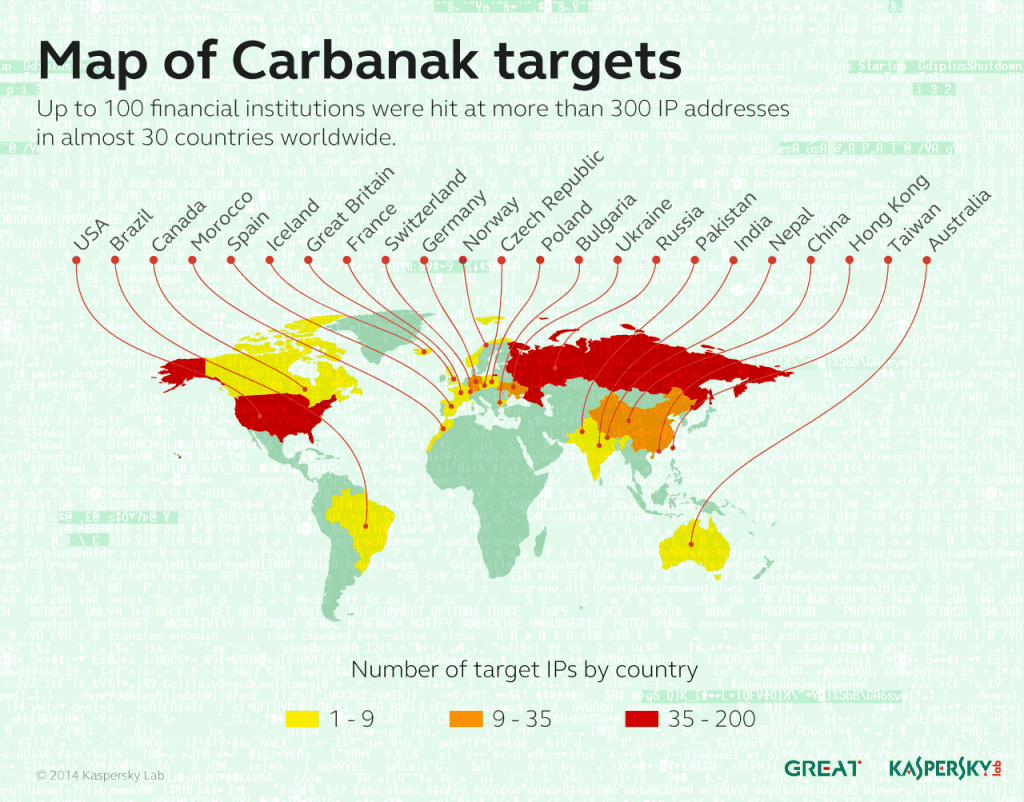
TIMELINE:
2013-2014: Carbanak emerges as a threat, launching attacks on financial institutions across multiple continents, including Europe, Asia, and North America.
2016: The Cobalt Group splinters from Carbanak, focusing on Eastern European and Russian banks, intensifying their attacks and refining their tactics.
2017: Carbanak/Cobalt Group continues to evolve, introducing new malware variants and tactics to evade detection and maintain their operations.
2020: Despite law enforcement efforts, the group remains active, demonstrating adaptability in response to cybersecurity countermeasures and continuing to target financial institutions globally.
IMPACT:
The Carbanak/Cobalt Group's activities have resulted in significant financial losses for targeted institutions, compromised customer data, and reputational damage. Their operations have highlighted the vulnerabilities present in banking systems and underscored the critical need for robust cybersecurity measures within the financial sector.
MEASURES TAKEN BY VICTIM COMPANY:
Enhanced Endpoint Security: Victim Company implemented advanced endpoint detection and response (EDR) solutions to detect and mitigate malicious activity across its network.
Network Segmentation: To limit the lateral movement of attackers, Vitime employed network segmentation, isolating critical systems and data from potentially compromised areas.
Threat Intelligence Sharing: Victim actively participated in threat intelligence sharing initiatives, collaborating with industry peers and law enforcement agencies to exchange information and strengthen collective defenses.
WHAT WE LEARNED:
Advanced Persistent Threats (APTs): Carbanak/Cobalt Group exemplifies the capabilities of APT groups, demonstrating persistence, sophistication, and adaptability in their operations.
Zero-Day Exploitation: The group's use of zero-day exploits and custom malware highlights the need for proactive security measures, including vulnerability management and patching.
Incident Response Readiness: Vitime's response to the threat underscores the importance of robust incident response plans and regular tabletop exercises to prepare for cyber attacks effectively.
PERSONAL TAKEAWAY:
The Carbanak/Cobalt Group's tactics serve as a stark reminder of the ever-present threat posed by sophisticated cyber adversaries. As cybersecurity professionals, we must remain diligent, continuously improving our defenses, and collaborating with industry peers to stay ahead of evolving threats.

CONCLUSION:
The Carbanak/Cobalt Group represents a formidable challenge to the financial sector, leveraging advanced techniques to target banks and financial institutions worldwide. However, through proactive security measures, threat intelligence sharing, and effective incident response capabilities, organizations can mitigate the risks posed by such cybercrime syndicates and protect the integrity of the financial system.

