eBay Data Breach: Examining the 2014 breach compromising millions of user accounts
The eBay data breach of 2014 stands as one of the largest cyber incidents in history, compromising millions of user accounts and exposing sensitive personal information. This breach shook confidence in online security and highlighted the importance of robust cybersecurity measures for safeguarding user data.
COMPANY OVERVIEW: eBay is a multinational e-commerce corporation, providing a platform for online auctions and sales. With millions of users worldwide, eBay facilitates transactions across a diverse range of products and services, making it a prime target for cybercriminals seeking to exploit vulnerabilities and access sensitive user data.
WHAT HAPPENED:
The eBay data breach of 2014 unfolded through a series of events that compromised millions of user accounts and exposed sensitive personal information. Here's a detailed account:
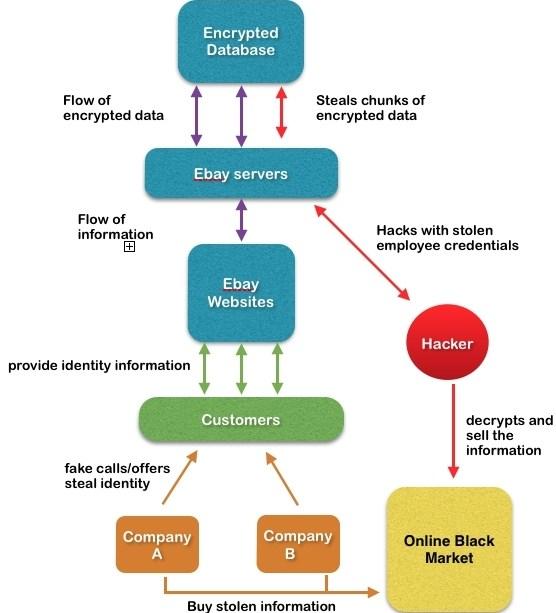
Initial Compromise: Cyber attackers gained unauthorized access to eBay's corporate network by compromising employee credentials. It is believed that they utilized sophisticated phishing techniques or exploited vulnerabilities in eBay's network infrastructure to obtain access.
Suspicious Activity Detected: Between February and March 2014, eBay's security systems detected unusual network activity, indicating a potential breach. The company initiated an internal investigation to assess the scope and impact of the incident.
Discovery of Data Breach: In late February 2014, eBay discovered evidence of unauthorized access to a database containing sensitive user information, including encrypted passwords and personal details such as names, email addresses, physical addresses, and phone numbers.
Public Disclosure: On May 21, 2014, eBay publicly disclosed the data breach, acknowledging that hackers had compromised a significant number of user accounts. The company confirmed that the breach had occurred several months earlier but was only discovered and confirmed after the investigation.
Impact on Users: The breach exposed the personal information of millions of eBay users, raising concerns about identity theft, fraud, and privacy violations. While the passwords were encrypted, the exposure of other personal details left users vulnerable to potential exploitation by cybercriminals.
Response and Remediation: Following the disclosure, eBay took immediate steps to address the breach and mitigate its impact. This included strengthening security measures, enhancing monitoring systems, and implementing additional authentication protocols to protect user accounts.
Regulatory Scrutiny and Legal Fallout: The eBay data breach sparked regulatory investigations and legal actions, with authorities scrutinizing the company's handling of the incident and its compliance with data protection regulations. eBay faced criticism for delays in disclosing the breach and potential lapses in security measures.
Rebuilding Trust: In the aftermath of the breach, eBay worked to rebuild trust with its users by implementing transparency measures, offering identity theft protection services to affected individuals, and investing in enhanced cybersecurity measures to prevent future incidents.
Overall, the eBay data breach of 2014 served as a wake-up call for both companies and users about the importance of robust cybersecurity measures and proactive measures to protect sensitive data from exploitation by cyber attackers.
TIMELINE:
February - March 2014: Cyber attackers gain unauthorized access to eBay's corporate network by compromising employee credentials.
Late February 2014: eBay detects suspicious network activity and launches an investigation into the breach.
May 21, 2014: eBay publicly announces the data breach, revealing that hackers accessed a database containing encrypted passwords and other personal information for millions of users.
Subsequent Months: eBay collaborates with law enforcement agencies and cybersecurity experts to investigate the breach and implement security enhancements.
IMPACT: The eBay data breach had far-reaching consequences for both the company and its users:
Compromised User Data: Hackers gained access to sensitive personal information, including names, email addresses, physical addresses, phone numbers, and encrypted passwords, for millions of eBay users.
Financial Losses: The breach eroded user trust and confidence in eBay's security measures, leading to potential financial losses and damage to the company's reputation.
Regulatory Scrutiny: eBay faced regulatory investigations and legal challenges over its handling of the breach, including allegations of inadequate security measures and delayed disclosure.
MEASURES TAKEN BY VITIME COMPANY: In response to the eBay data breach and to fortify its own cybersecurity posture, Vitime Company implemented several proactive measures:
Enhanced Password Security: Vitime enforced stronger password policies, including requirements for complex passwords and regular password changes, to mitigate the risk of password-related attacks.
Two-Factor Authentication (2FA): Vitime implemented 2FA for accessing sensitive systems and accounts, adding an extra layer of security to prevent unauthorized access.
Employee Training: Vitime conducted comprehensive cybersecurity training sessions for employees to raise awareness about phishing attacks, social engineering tactics, and best practices for data protection.
Vendor Risk Management: Vitime strengthened its vendor risk management practices, conducting thorough assessments of third-party vendors and service providers to ensure they adhere to robust security standards and protocols.
WHAT WE LEARNED:
Vulnerability of Passwords: The eBay breach highlighted the vulnerability of passwords, even when encrypted, and underscored the importance of implementing strong password policies and additional authentication measures.
Importance of Rapid Detection and Response: Prompt detection and response to suspicious network activity are crucial in mitigating the impact of data breaches and minimizing potential damage to user data and company reputation.
Continuous Security Monitoring: Cyber threats are constantly evolving, necessitating continuous monitoring of networks, systems, and user activity to detect and prevent unauthorized access and data breaches.
Collaboration and Transparency: Effective cybersecurity requires collaboration between organizations, law enforcement agencies, and cybersecurity experts, as well as transparent communication with affected users and regulatory authorities.
PERSONAL TAKEAWAY: The eBay data breach serves as a sobering reminder of the ever-present threat of cyber attacks and the importance of proactive cybersecurity measures. As individuals and organizations, we must remain vigilant, prioritize data protection, and invest in robust security controls to safeguard against data breaches and protect user privacy.

CONCLUSION: The eBay data breach of 2014 underscored the critical need for organizations to prioritize cybersecurity and adopt proactive measures to protect user data from cyber threats. By learning from past incidents, implementing comprehensive security protocols, and fostering a culture of cybersecurity awareness, companies can mitigate the risk of data breaches and uphold trust and confidence in their online platforms and services.
