Table of contents
- Common types of malware and their characteristics
- The dangers of malware and its impact on businesses and individuals
- How malware spreads and infects systems
- Prevention techniques and best practices to protect against malware
- Introduction to anti-malware software and its importance in cyber security
- Different types of anti-malware tools and their features
In today's digital age, cyber security has become a paramount concern for businesses and individuals alike. Malware, short for malicious software, is a common and persistent threat that can wreak havoc on computer systems and networks. Understanding the different types of malware is essential to safeguarding against potential cyberattacks.
Malware refers to a broad category of software programs that are designed to infiltrate or damage a computer system without the user's consent. It can take various forms, including viruses, worms, Trojans, ransomware, and spyware. Each type of malware has its own unique characteristics and methods of propagation, making it crucial to be able to identify and mitigate these threats effectively.
Common types of malware and their characteristics
Viruses: Viruses are a form of malware that infects files or programs by attaching themselves to them, spreading from one computer to another. They can cause a wide range of issues, such as corrupting or deleting files, disrupting system operations, and even stealing sensitive information.
Worms: Unlike viruses, worms can spread without the need for a host file or program. They exploit security vulnerabilities in computer networks to self-replicate and spread rapidly. Worms can consume network bandwidth, overload systems, and create backdoors for further exploitation.
Trojans: Trojans masquerade as legitimate software or files, tricking users into downloading or executing them. Once inside a system, Trojans can enable unauthorized access, steal personal information, or install additional malware.
Ransomware: Ransomware is a particularly malicious type of malware that encrypts files on a victim's computer, rendering them inaccessible. The attacker then demands a ransom in exchange for restoring access to the files. Ransomware attacks can have devastating consequences for businesses and individuals, leading to data loss and financial damages.
Spyware: Spyware is designed to secretly monitor a user's activities, often with the intent of collecting sensitive information such as login credentials or financial data. It can be used for various purposes, including identity theft, corporate espionage, or targeted advertising.
The dangers of malware and its impact on businesses and individuals
The presence of malware poses significant risks to both businesses and individuals. For businesses, malware attacks can result in financial losses, damage to reputation, and legal implications. A successful malware attack can lead to data breaches, where customer or employee information is compromised, resulting in severe financial and legal consequences. Additionally, malware can disrupt business operations, leading to downtime and reduced productivity.
Individuals are also vulnerable to the dangers of malware. Personal information, such as credit card details or login credentials, can be stolen and used for identity theft or financial fraud. Malware can also cause personal files to become corrupted or lost, leading to emotional distress and inconvenience.
Moreover, the impact of malware extends beyond immediate financial and personal consequences. The loss of trust in digital systems and the fear of potential cyber-attacks can have long-lasting effects on overall confidence in online transactions and communication.
How malware spreads and infects systems
Understanding how malware spreads and infects systems is crucial to developing effective prevention strategies. Malware can enter a system through various means, including:
Email attachments: Malicious attachments in emails are a common method of malware distribution. Users are often tricked into opening these attachments, which contain the malware payload.
Infected websites: Visiting compromised or malicious websites can lead to malware infections. Drive-by downloads, where malware is automatically downloaded without the user's consent, are a prevalent form of web-based malware attack.
Removable media: USB drives or other portable storage devices can carry malware, which can be inadvertently transferred to a computer when connected.
Software vulnerabilities: Exploiting vulnerabilities in software or operating systems is another way malware can infiltrate a system. It is crucial to keep software and systems up-to-date with the latest security patches to minimize the risk of such attacks.
Once inside a system, malware can propagate and spread to other computers or devices through various means, including network connections, shared files, or remote access capabilities. Some malware can also remain dormant, waiting for specific conditions or triggers to activate and cause harm.
Prevention techniques and best practices to protect against malware
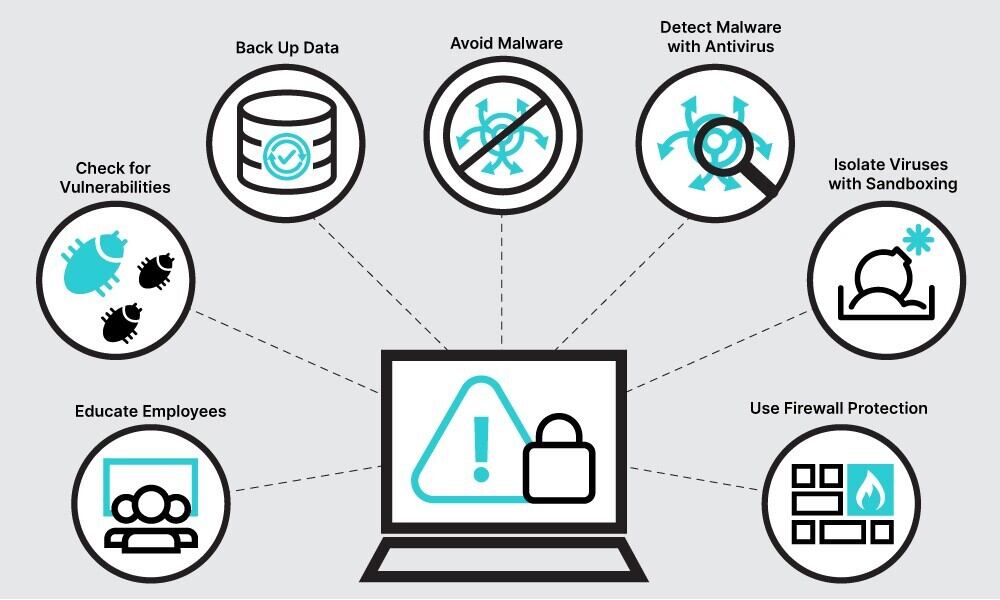
WPrevention is key to mitigating the risks posed by malware. Employing the following techniques and best practices can significantly enhance your defenses against malware attacks:
Educate users: Providing training and awareness programs to users regarding the risks of malware and safe computing practices is essential. Users should be cautious when opening email attachments, visiting websites, or downloading files from untrusted sources.
Use strong passwords: Enforcing the use of strong, unique passwords for all accounts can prevent unauthorized access to sensitive information.
Keep software up to date: Regularly updating software and operating systems with the latest security patches helps protect against known vulnerabilities that malware can exploit.
Implement firewalls and network security: Firewalls act as a barrier between your computer and the internet, monitoring and blocking malicious traffic. Network security measures, such as intrusion detection systems and secure Wi-Fi configurations, can further enhance your defenses.
Backup data regularly: Regularly backing up important data ensures that you can recover your files in case of a malware attack. Backups should be kept offline or on a separate network to prevent malware from infecting them.
Introduction to anti-malware software and its importance in cyber security
While prevention techniques are crucial, they cannot guarantee complete protection against malware. This is where anti-malware software plays a vital role. Anti-malware software is designed to detect, prevent, and remove malware from computer systems. It provides an additional layer of defense against the ever-evolving threat landscape.
Without proper anti-malware protection, your computer systems are susceptible to malware infections that can result in significant damage, both financially and operationally. Investing in reliable anti-malware software is a proactive step towards ensuring the security of your digital assets.
Different types of anti-malware tools and their features
There are various types of anti-malware tools available on the market, each with its own set of features and capabilities. Understanding the different types can help you choose the right one for your specific needs. Here are some common types of anti-malware tools:
Antivirus software: Antivirus software is designed to detect and remove viruses from computer systems. It scans files, programs, and email attachments for known virus signatures and suspicious behavior.
Anti-spyware software: Anti-spyware tools detect and remove spyware from systems. They monitor processes and network activity, identifying and blocking attempts to collect sensitive information.
Firewall software: Firewalls act as a barrier between your computer and the internet, monitoring network traffic and blocking unauthorized access. They can also detect and block incoming malware threats.
Behavior-based detection tools: These tools analyze the behavior of programs and files to identify potential malware. They can detect zero-day threats that have not yet been identified by traditional signature-based detection methods.
Browser protection plugins: Browser plugins and extensions can provide additional protection against web-based malware threats. They can block malicious websites, warn against suspicious downloads, and prevent unauthorized tracking.

