SolarWinds Supply Chain Attack: Exploring the 2020 breach affecting numerous government agencies and companies.
The SolarWinds supply chain attack, which occurred in 2020, was a significant cybersecurity incident that impacted numerous government agencies and companies. Here's an overview:
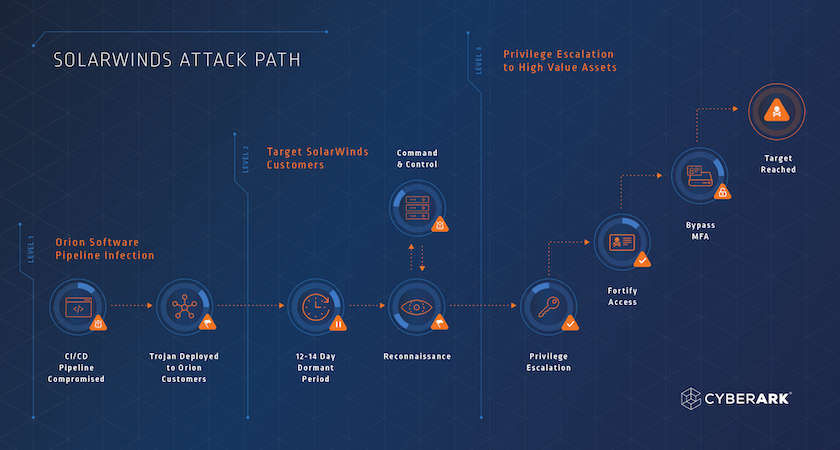
What Happened: Hackers infiltrated the software supply chain of SolarWinds, a major provider of network management software. They inserted malicious code into the company's software updates, specifically the Orion platform, which is widely used for network monitoring.
Scope of the Attack: The attack affected thousands of SolarWinds customers who downloaded and installed the compromised software updates. This included numerous U.S. government agencies, such as the Department of Defense, the Department of Homeland Security, and the Treasury Department, as well as private companies worldwide.
Method of Attack: The attackers used a sophisticated supply chain compromise technique, whereby they targeted SolarWinds' software development process to inject malicious code into legitimate software updates. This allowed them to gain access to the networks of organizations using the compromised software.
Impacts: The breach had severe consequences, including unauthorized access to sensitive information, potential espionage, and the disruption of critical systems. It raised concerns about the vulnerability of software supply chains and the ability of adversaries to exploit them for cyberattacks.
Investigations and Attribution: Following the discovery of the breach, extensive investigations were conducted by government agencies, cybersecurity firms, and independent researchers to understand the scope and attribution of the attack. While initial evidence pointed to a state-sponsored group linked to Russia, attribution remained a complex and ongoing process.
Response and Mitigation: In response to the breach, affected organizations took steps to contain the attack, remove the compromised software, and enhance their cybersecurity posture. There were also calls for improved cybersecurity practices, increased transparency in supply chains, and international cooperation to address similar threats in the future.

Overall, the SolarWinds supply chain attack highlighted the importance of securing software supply chains, detecting and responding to cyber threats effectively, and fostering collaboration among stakeholders to mitigate the impact of such incidents.

Several key lessons were learned from the SolarWinds supply chain attack:
Supply Chain Security: The incident underscored the critical importance of supply chain security in the cybersecurity landscape. It demonstrated how adversaries can exploit trusted software vendors to compromise the networks of their customers. Organizations now recognize the need to assess and mitigate risks throughout their supply chains, including vetting third-party vendors and monitoring software updates for signs of tampering.
Detection and Response: The attack highlighted the need for improved detection and response capabilities. Many organizations were unaware of the breach for an extended period, allowing the attackers to maintain access and exfiltrate sensitive data. Enhancing threat detection mechanisms, implementing robust incident response plans, and conducting thorough forensic investigations are essential for minimizing the dwell time of attackers and mitigating the impact of breaches.
Zero Trust Architecture: The concept of zero trust architecture gained prominence in the aftermath of the SolarWinds attack. Adopting a zero trust approach means verifying and validating every request for access to resources, regardless of the source or location of the request. This helps mitigate the risk of lateral movement by attackers within compromised networks and reduces the potential impact of breaches.
Information Sharing and Collaboration: The incident highlighted the importance of information sharing and collaboration among organizations, government agencies, and cybersecurity professionals. Sharing threat intelligence, best practices, and lessons learned can help enhance collective defenses against sophisticated cyber threats. Building trust and fostering partnerships within the cybersecurity community are crucial for effectively addressing evolving threats.
Regulatory and Policy Changes: The SolarWinds breach prompted calls for regulatory and policy changes to strengthen cybersecurity standards and accountability. Governments and regulatory bodies may introduce new regulations or guidelines to improve software supply chain security, enhance incident reporting requirements, and incentivize organizations to invest in cybersecurity resilience measures. Compliance with these regulations and adherence to industry best practices can help organizations better protect against cyber threats.

